The Foglight Experience Viewer captures all user interactions, even if it's not really a user interacting with your site. Many hackers are (right now) attempting to execute code via script injection into your public-facing site. They are trying this with different browser types just in case your site acts differently depending on the browser, and they are going through all steps up until actually placing an order or booking travel. It's typical at these pages where billing information is entered and processed that the hackers are able to uncover key flaws or vulnerabilities within the site they can later use to exploit. This type of execution is not really a denial of service attack (DOS), in fact most hackers will stay away from this type of exposure since there are plenty of firewalls and intrusion prevention systems on the market today to stop this. Instead, they opt for a frequency of about 5-10 minutes apart to fly under the radar.
From a business perspective, even if your site is 100% secure, this can wreak havoc in a few ways:
1. Many inventories are just-in-time and held for the duration of the session. If a scripter is booking a hotel room for the week, your inventory may be temporarily depleted until the user enters successful payment information, perhaps for up to 30 minutes. If this scripter is consistently booking the same property this could severely impact actual availability and deter actual customers from booking.
2. Conversion rates are looking worse now. Booking and conversion rates are based on getting a customer from point A to point E in a booking/purchasing process. If a scripter is taking your site from point A to point D for instance, stopping just before booking, your ultimate conversion rates are going to fall through the floor and it will likely be difficult for your team to understand why.
3. Site performance degrades with many unnecessary searches and inventory pulls as the hacker does their thing.
What can you do?
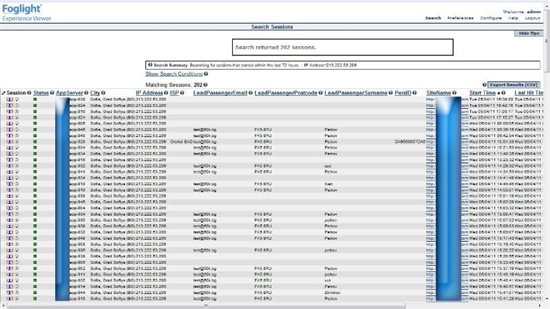
Foglight is NOT a security-based IPS or IDS, but rather an Application Performance Management and Marketing/Operations support tool. We do not market ourselves in the security space. However, many customers are using Foglight as a quick way to prove or validate suspected fraud cases. This type of fraud support could quickly understand that conversion rates are down because there is ONE scripter on the site chewing up transactions, for instance. In the screenshot below, taken from an actual customer (names redacted), you can see that a scripter has hit the site 202 times in the last 72 hours. Foglight can determine that the attack is coming from Sofia, Bulgaria, about every 15 minutes. Each line in the picture represents a user session from the same user in Bulgaria. When we dug deeper here, we found that the browser type was changing from IE6 to IE7 to IE8, Firefox, and others. This is likely to help the scripter find vulnerabilities that are browser-specific, or to throw off the IPS/IDS systems as mentioned.
Once we reviewed a few sessions we could see the data entered was exactly the same, shown with his fictitious email and passenger details below. In each case, the scripter was booking hotels and airfare, getting to the very last step in the process, then abandoning the session. With Foglight Experience Viewer (FxV) searches can quickly reveal these types of attacks, even if there were no performance or availability issues with these sessions. Since FxV stores EVERY hit from EVERY user, this data is immediately available for query. Note the query in this case was simply the IP address. We could have asked FxV, "how many users got to step D today and DID NOT get to the final step E?" Once you are able to see clearly fraudulent information returned in a query like that, further investigation can ensue.
--Jason
Jason Trunk is an end-user performance expert with Quest Software and can be reached on Twitter @EarlofURL