A few weeks ago, my colleague John O’Boyle posted that there is no end to endpoint management. That’s no secret to system administrators who spend most of their time thinking about mobile device management, endpoint security, security patches and software deployment to an ever-growing variety of device types.
Tech evangelist Tim Warner and I explored the topic even more deeply in a webcast called Predicting the Future of Endpoint Management in a Mobile World. In this post, I’ll recap the main points of our discussion.
How we got to endpoint management
An endpoint device is defined as an internet-capable piece of hardware connected to a TCP/IP network. (It’s been a long time since all it meant was “a computer.”) In other words:
- Server and desktop PCs (Windows, Linux, macOS)
- Laptop PCs
- Thin-client devices (Chromebooks)
- Tablets
- Smartphones (iOS, Android)
- Printers
- Point-of-sale (POS) systems
- Internet of Things devices (including smart meters, appliances and voice assistants)
IT now cuts most endpoints with the knife of ownership, telling employees, “bring your own device.” The BYOD policy of permitting employees to bring personally owned devices to their workplace, and to use those devices to access privileged company applications and data, has generated a lot of conversations in IT. On the other hand, the devices may be customer-owned and personally enabled (COPE). The company purchases the devices, provides them to its employees and enables private-device functions for some personal use.
Under either policy, sysadmins still have to secure the network, infrastructure, applications and systems from access by potentially untrusted users with the device in their hand.
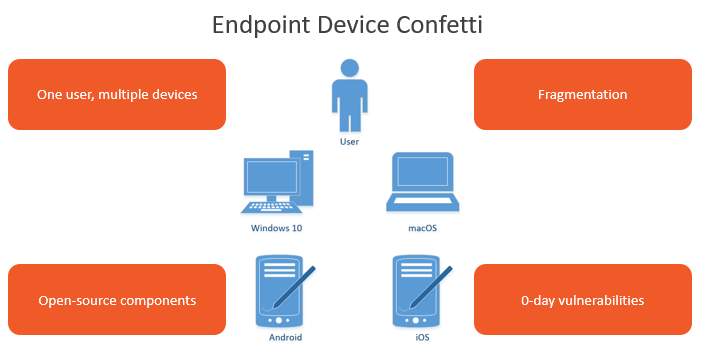
Endpoint device confetti
Also under either policy, sysadmins have to manage the devices. As shown below, several factors make that more difficult: the variety of devices assigned to an individual user, OS fragmentation, free and open-source components in software, and zero-day vulnerabilities for which the vendor hasn’t yet released a patch.
The resulting confetti of endpoint management combinations puts sysadmins in the position of jumping from one dedicated console to another. That makes it difficult for them to have a full overview of their endpoint landscape. It goes far beyond management by spreadsheet or even by most help desk applications.
And if they don’t know about all their endpoints, then they certainly don’t know about all their endpoint security. They lack three important things:
- Insight – Can they see all endpoints, in all their forms, through a single pane of glass?
- Policy – How well documented is their inventory? How easily could they produce reports showing compliance?
- Enforcement – How can they detect and remediate compromised systems?
To keep up with all the change in their environment, they would need a comprehensive view of all of their devices from a single console, and the ability to manage the onboarding, upgrades and lifecycle events for each endpoint device.
Endpoint management wish list
What are the most important features when it comes to considering an endpoint management solution?
- Asset management means inventory: knowing what you have, how much of what you have, what’s being used and what’s idle.
- Patch management shows whether your hardware and software assets are updated with current security patches to keep you ahead of vulnerabilities.
- All operating systems get upgraded eventually. Even new installs require licensing. Operating system deployment (OSD) manages that.
- Once the operating system is in place, you have to white-list, deploy and manage individual applications or sets of applications.
- Depending on your geography and industry, your devices may be subject to compliance with regulations, and endpoint management should facilitate that.
- In the age of the tech-savvy user, it’s a good idea to offer some measure of self-service management. Take advantage of employees’ desire for partial ownership in endpoint systems management and support them as efficiently as possible.
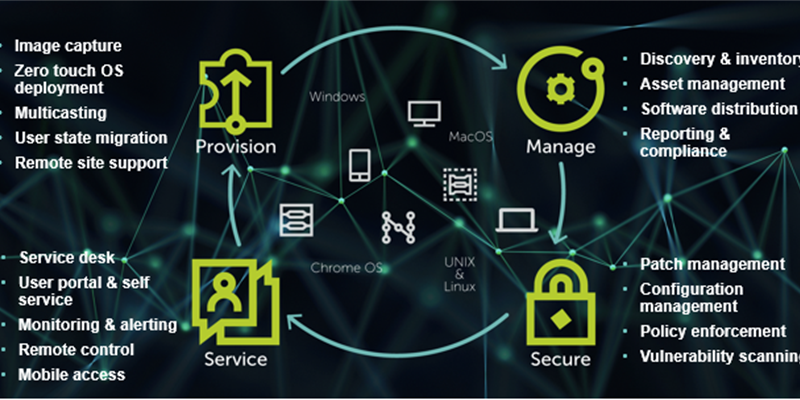
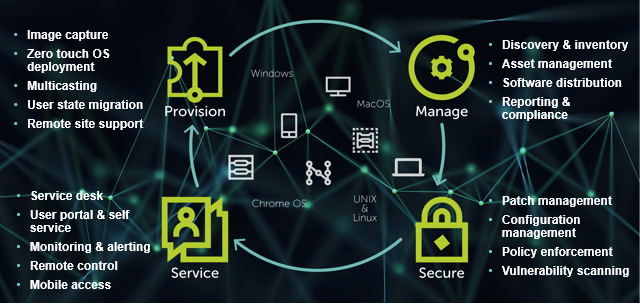
Most of all, keep in mind the systems management lifecycle, during which sysadmins have to provision, manage, secure and service all endpoint devices:
The lifecycle applies to all the endpoint devices in your current environment and those that will enter it in the future. Admins should keep those stages in mind in all their buying decisions.
Webcast: “Predicting the Future of Endpoint Management in a Mobile World”
Grab the highlights from the webcast that Tim Warner and I conducted, Predicting the Future of Endpoint Management in a Mobile World for more perspective on how quickly the sand is shifting under the feet of all system administrators. The webcast includes an introduction to the KACE appliances from Quest® and a deep-dive Q&A with IT admins who ask the same kind of questions you ask.